Revolutionizing Banking Security With Zero Trust Architecture

At a conference in India recently, Visa Global CEO Ryan McInerny revealed that Visa is attacked between 400 and 500 million times in a month, with the attack vectors originating from across the world1. Specific to the US, a November 2023 security breach at a third-party service provider affected over 57000 Bank of America customers2 and became a clarion call for a renewed cybersecurity approach as financial institutions become more digitized and interconnected than ever. In the face of such unprecedented cybersecurity challenges, the adoption of Zero Trust Architecture (ZTA) emerges as a strategic imperative for senior banking executives.
Classic perimeter-based security models face several challenges in today’s distributed and cloud-based environments. Traditional models operate on a “trust but verify” principle, assuming trust within the network once authenticated. ZTA represents a paradigm shift from this model, assuming breach, and verifying each request as if it originates from an open network. Our webinar on this topic, Revolutionizing Banking Security, delves deeper into the differences between traditional and zero trust security models.
This blog introduces the foundational pillars of ZTA and implementation best practices that can help banking technology professionals, cybersecurity experts, and IT leaders in the financial sector transform the security landscape of their institutions.
Zero Trust Architecture as a strategic investment for banks
Cybersecurity defense ranks very high on financial institutions’ worry list, and this is evident in the escalating investment trends. Banking and capital markets institutions spent 0.80% of their revenue on cybersecurity in 2023, up from 0.30% in 20193. In this context, the shift to ZTA has become critical for banks today due to several key factors:
- Evolving Threat Landscape: Traditional perimeter-based security, where trust is granted once inside the network, struggles with today’s sophisticated cyberattacks. Hackers target any vulnerability and, once inside, can move laterally through the network, accessing sensitive data. ZTA’s “never trust, always verify” approach mitigates this risk by continuously verifying users, devices, and applications before granting access, minimizing the damage from breaches.
- Increased Attack Surface: Banks are adopting cloud environments, mobile access, and interconnected systems, expanding their attack surface. Securing all these entry points is complex. ZTA simplifies security by focusing on least privilege access and micro-segmentation, limiting access to specific resources based on user identity, device, and context.
- Regulatory Compliance: Data privacy regulations like GDPR and CCPA are driving stricter data security requirements. ZTA helps banks comply by providing granular control over data access and audit trails for easier tracking and accountability.
- Protecting Sensitive Data: Banks hold vast amounts of sensitive customer data, making them prime targets. ZTA strengthens data security by minimizing lateral movement and unauthorized access, reducing the risk of data breaches and financial losses.
- Improved User Experience: By eliminating the need for constant logins and password changes, ZTA can improve user experience for employees and customers by providing secure access based on context and risk, streamlining workflows.
- Future-Proofing Security: As technology evolves, ZTA’s flexible and adaptable framework can easily accommodate new technologies and changing security needs, ensuring long-term security without needing major security overhauls.
Core tenets of Zero Trust security
The core principles of Zero Trust form the foundation of a security strategy that insists on the continuous verification of all entities within an organization’s network. These principles are critical for developing a resilient cybersecurity posture that can adapt to evolving threats and protect sensitive data and resources (Image 1).
Image 1
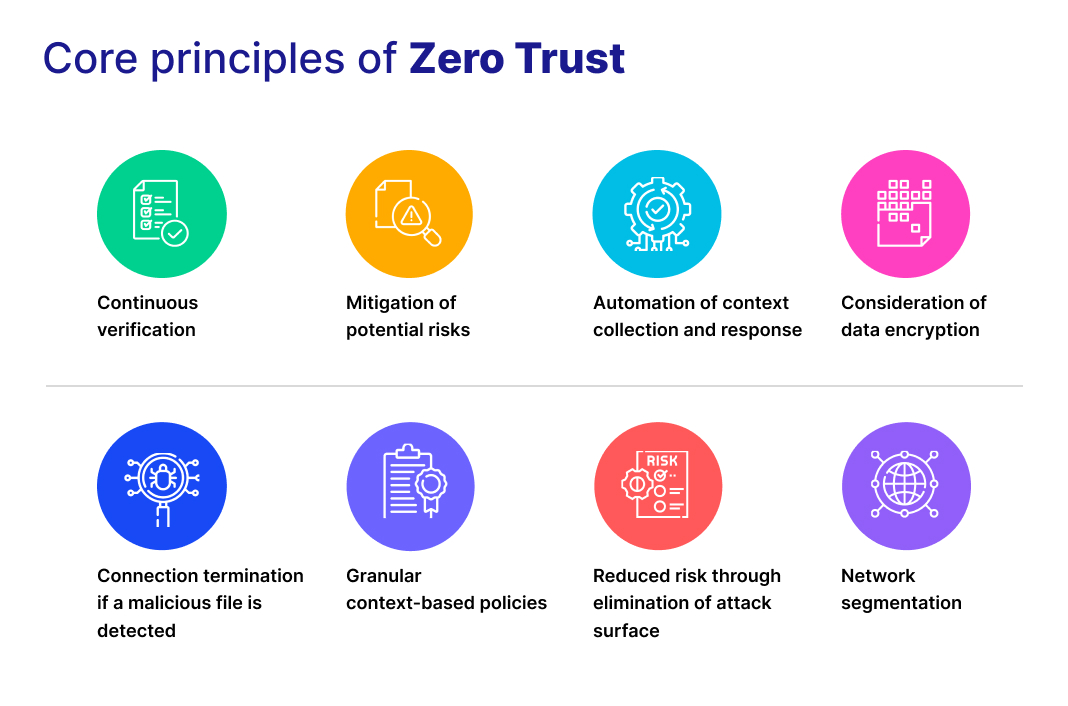
Implementing Zero Trust successfully requires you to incorporate, coordinate, and integrate a challenging combination of policies, practices, and technologies. A conceptual security model, such as foundational pillars, can help understand and organize those components4. (Image 2)
Image 2
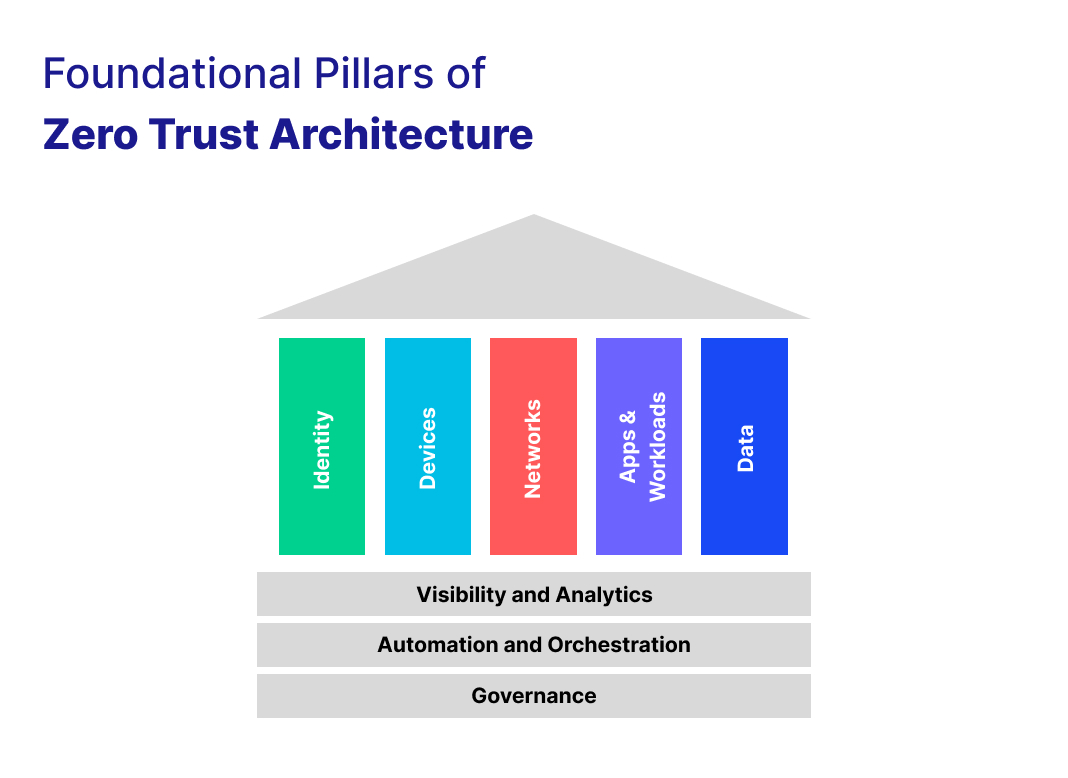
Let’s understand how ZTA’s foundational pillars address the critical elements of security in a Zero Trust environment:
Identity Pillar
This pillar emphasizes the need for advanced identification methods using multiple criteria and attributes for identification (like multi-factor authentication) to suit the dynamic security landscape.
Device Pillar
ZTA requires that all devices or endpoints used by consumers be identified, verified, and compliant before they can initiate connections to sensitive or critical services. This means fortifying all enterprise devices with strong endpoint protection.
Network Pillar
Given the inadequacy of legacy perimeter-based network isolation, ZTA focuses on micro-segmentation, multi-level security controls, and strong traffic encryption for securing the network against internal and external threats.
Data Pillar
ZTA mandates strong cryptographic encryption for all critical data, regardless of its location, form, or state. This ensures the protection of data across the digital infrastructure, safeguarding it against unauthorized access and breaches.
Visibility and Analytics Pillar
This pillar emphasizes continuous monitoring and robust observability across all aspects of ZTA, with a focus on detecting threats and applying proactive measures to maintain a high level of vigilance.
Automation and Orchestration Pillar
The automation and orchestration pillar highlights the need for automation to achieve error-free deployments and maintain security standards, minimizing human error.
Governance Pillar
This pillar underlines the importance of robust Governance, Risk, and Compliance Management (GRC) practices to ensure regulatory compliance and risk management.
Implementation strategies and best practices
Implementing ZTA involves several steps, starting with defining the protected surface, mapping the transaction flows, architecting a Zero Trust network, creating a Zero Trust policy, and monitoring and maintaining the network. Organizations should also consider the role of cloud services and encryption in enhancing security. Let’s deep dive into the best practices of ZTA implementation at Zeta.
Zeta’s ZTA implementation for banks demonstrates a forward-thinking approach to cybersecurity, leveraging Open Source Software (OSS) best practices and toolchains to create a secure, resilient, and compliant digital infrastructure. This model serves as a valuable reference for financial institutions aiming to achieve a highly secured, compliant, cloud-native, and API-driven infrastructure.
Image 3
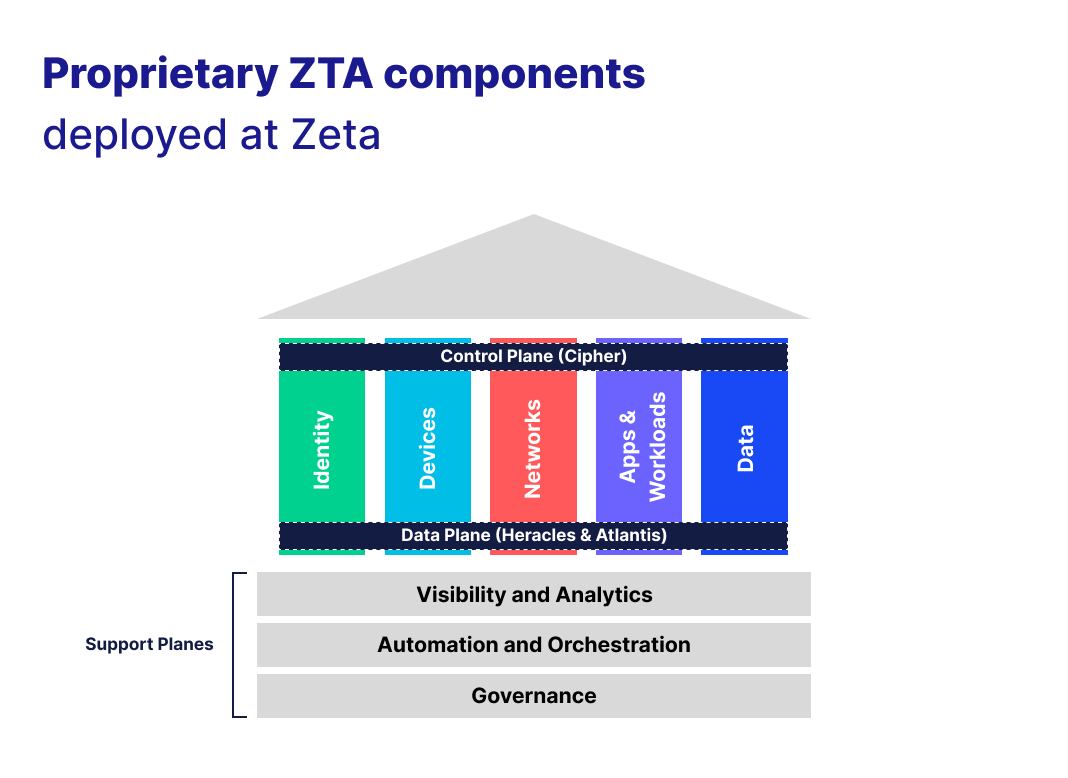
Control Plane: Cipher
Zeta’s control plane, named Cipher, serves as a multi-attribute/multi-factor based API-driven identity access and key management system. Cipher acts as the central control plane for Zeta’s Zero Trust Architecture, ensuring secure identity access management across all aspects of the infrastructure.
Data Plane: Heracles and Atlantis
For the data plane, Zeta developed two tools, Heracles and Atlantis, which together form the backbone of our ZTA data management strategy. Heracles is responsible for identity-aware traffic management, while Atlantis provides robust data plane functions, including multi-level access control and cryptographic operations, ensuring that only just-in-time and just-enough access is granted to trusted consumers.
External/Support Plane: Olympus World Control Center (OWCC), RoseCI, Orcus and Centaur
The external or support plane incorporates tools designed to enhance observability, automation, and governance:
- OWCC: An observability and analytics platform for monitoring, alerting, and reporting unusual activities, thereby enhancing the visibility and analytics pillar of Zero Trust.
- RoseCI: A tool focused on Secure Software Development Life Cycle (SSDLC) with a shift-left approach, emphasizing automation and orchestration to ensure error-free deployments.
- Orcus: A financial fraud and risk management engine, highlighting Zeta’s commitment to governance, risk, and compliance (GRC) within the ZTA ecosystem.
- Centaur: An InfoSec GRC and SIEM engine, further bolstering Zeta’s governance capabilities and ensuring compliance with relevant standards and regulations.
Olympus is Zeta’s Private Portable cloud-agnostic Platform-as-a-Service (PaaS) layer. It simplifies common concerns like multi-tenancy, logging, monitoring, tracing, data and event streaming by abstracting infrastructure concerns and offering banks a standardized and governed interface across banking and payments applications.
OWCC provides a central hub for the observability and analysis of Olympus system performance. Its Zone navigator offers 360-degree visibility into the health and performance across Olympus platform services and SaaS products, ensuring smooth operation and stability.
Learn more about how Zeta’s adoption scales the ZTA implementation maturity model in our webinar on this topic, Revolutionizing Banking Security.
3 step Zero Trust implementation approach for banks
Zero Trust Architecture offers a comprehensive and adaptive approach to cybersecurity, addressing the limitations of traditional security models and meeting the needs of modern financial institutions. By implementing ZTA, banks can significantly enhance their security posture, reduce the risk of breaches, and adapt more effectively to the evolving landscape of cyber threats.
To begin your bank’s journey towards mature Zero Trust security infrastructure, prepare your implementation roadmap using the following approach:
Step 1
Establish a strong foundation for Zero Trust implementation with preparatory steps:
- Security Landscape Assessment: Identify weak spots and best practices to map a secure course of action.
- Sensitive Data Identification: You need to identify critical data that needs to be secured, and apply top-notch encryption for ultimate protection.
Step 2
Once the groundwork is laid, implement Zero Trust across all your domain resources:
- Applications: Each app should act as a vigilant gatekeeper, granting access only to authorized individuals with the right credentials.
- Infrastructure: Your infrastructure should resemble a fortified castle, with robust access controls ensure only authorized personnel can enter critical systems.
- Networks: You need to ensure that data travels through secure tunnels, shielded by encryption and granular controls.
Step 3
Stay vigilant, and adapt. Zero Trust is an ongoing process, not a one-time fix. It is critical that you constantly refine your approach, embracing new technologies to navigate towards an impregnable digital future.
Contact Us to know how we deliver secure, cloud-native and API-first issuer processing, compliant with Zero Trust principles.
Footnotes
- CNN-News 18, Rising Bharat Summit 2024 | January 2024
- Security Magazine, Security experts discuss recent Bank of America data breach | February 2024
- Deloitte Global, Cybersecurity Insights 2023 | October 2023
- ACT-IAC, Zero Trust Cybersecurity Current Trends | April 2019


